
A group of cyber-criminals created 28 fake ad agencies and bought over 1 billion ad views in 2017, which they used to deliver malicious ads that redirected unsuspecting users to tech support scams or sneaky pages peddling malware-laden software updates or software installers.
The entire operation —codenamed Zirconium— appears to have started in February 2017, when the group started creating the fake ad agencies which later bought ad views from larger ad platforms.
These fake ad agencies each had individual websites and even LinkedIn profiles for their fake CEOs. Their sole purpose was to interface with larger advertising platforms, appearing as legitimate businesses.
How the operation worked
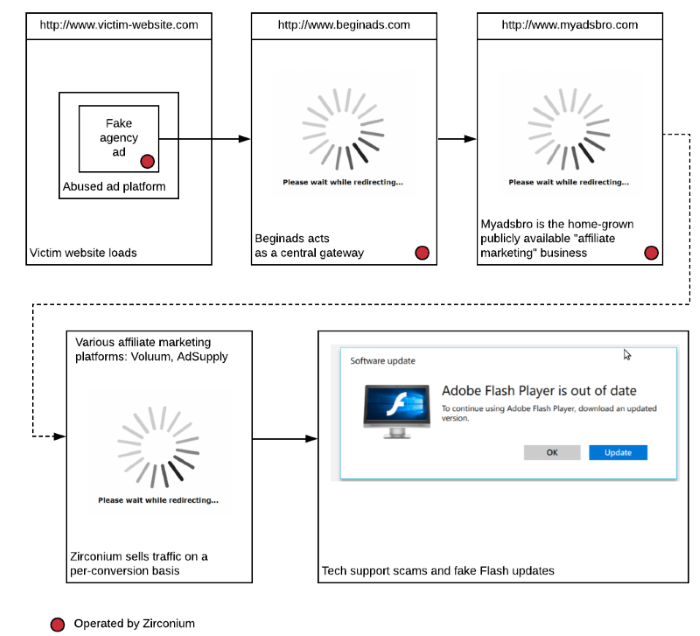
The image below describes how the group operated. The fake ad agencies would buy ads displayed on legitimate sites via these ad platforms.
These ads would allow the Zirconium group to run JavaScript code that executed a "forced redirect," effectively hijacking visitors off the original site to an intermediary domain. This intermediary domain would fingerprint and classify incoming traffic, then redirect the user to another domain, also operated by Zirconium.
Crooks would use this third domain as an affiliate traffic jump-off point, allowing others to buy the traffic they hijacked from legitimate sites.
In many cases, users were redirected to pages offering fake (malware-laced) Flash updates, websites offering (malware-infested) software installers, tech support scams, or other scareware pages.
Ad security company Confiant, the one who discovered this entire operation, says ads bought by this group reached 62% of ad-monetized websites on a weekly basis.
All in all, Confiant believes that about 2.5 million users who've encountered Zirconium's malicious ads were redirected to a malicious site, with 95% of the victims being based in the US.
Eight fake ad agencies still dormant
The entire operation flew under the radar for most of the time but became harder to ignore as it grew and researchers started to detect more and more aggressive user fingerprinting scripts.
Dangu says the group exclusively targeted desktop browsers, ignoring mobile traffic. The user's operating system did not count, the group going after Windows, Linux, Mac, or ChromeOS users alike.
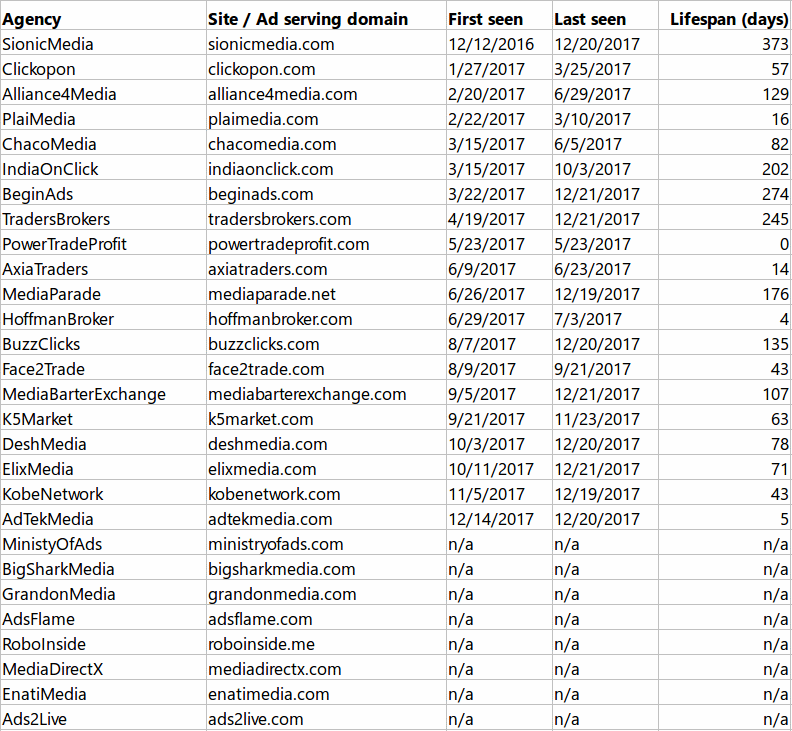
The Confiant CTO also says Zirconium used only 20 of its 28 fake ad agency identities for this operation, and eight remained dormant earlier this week when Confiant published its Zirconium exposé.
Malvertising crews using fake ad companies may be a new concept for the casual infosec-passionate reader, but conversations this Bleeping Computer reporter had with industry experts last year revealed that most experts knew this was happening, but they hadn't managed to get all the details together to expose this growing trend.
Besides blowing the lid on this new tactic, Dangu also pointed out another interesting fact; that this malvertising campaign was nothing like previous operations, which mostly sent traffic to exploit kits.
Dangu believes that improved browser security features now make most exploit kits ineffective. In addition, the decision from most browser makers to change Flash into a disabled state or click-to-run policy have also contributed to the demise of classic malvertising+exploit kit campaigns.
Chrome 64, released earlier this week, blocks the forced redirect technique (also known as tab-under) used by the Zirconium group.
8 Common Threats in 2025
While cloud attacks may be growing more sophisticated, attackers still succeed with surprisingly simple techniques.
Drawing from Wiz's detections across thousands of organizations, this report reveals 8 key techniques used by cloud-fluent threat actors.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now